Enterprise Edition
(Coming Soon!)
Centralized Artifact Repository
Team Collaboration
Report Generation
Tool Integration

See your organziation through the eyes of a hacker.
The Enterprise Edition of the ThreatConsole is designed to organize complex vulnerability data that maps to your Enterprise's business heirarchy. You can create custom heirarchies with complex branch and leaf structures. When a suboridate business unit has a security issue, it will be observed at the top branch level (in reality, if one host has a single vulnerability, the entire infrastructure is potentially at risk.) You can assign each Target Group customized teams for vulnerabliity discovery and threat monitoring (Red/Blue Teams) as well as vulnerability remediation teams (sys admins and developers.) We are working to integrate SIEM data from server logs, Intrusion Detection Systems, and other sources also.
The Enterprise Edition also offers an interactive flythru interface depicting networks in a way that not only shows the inventory, but also highlights security issues and their potential impact. Clicking on any service or system displays the security issues associated with it. Heads up displays provide other relavent technical information. The flythru interface is a great visual aid for non-technical people (executives and board members) who may not fully understand what services are or even what an IP address is, but it also provides an alternate view for security pros who may be tired of looking at scan outputs, spreadsheets, and tables or if they just want a quick view of the network to make sure everything was captured during scanning. Traditional boring views are also available!
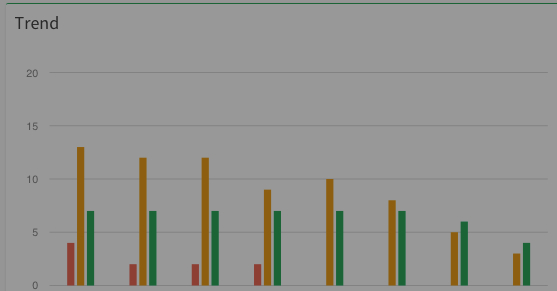
Track the progress of your security program
Identifying and resolving security issues is what the Enterprise Edition is all about. As vulnerabilities are mitigated you will see the attack profile decrease as your infrastructure becomes more secure over time. Show management teams, executives, and board members, the value that is provided by the security program!
Have multiple users working with the same data
Share your Enterprise data with subcontractors that you collaborate with on an assessment/penetration tests or incident response engagements on a project by project basis. You can restrict who can see what and revoke access at any time. You can make private comments with just your team members and also be able utilize the collective wisdom of the community. If you have a large organziation with multiple groups that have different areas of responsibilty, you can restrict individual team members so they can only see data they are responsible for. This could help avoid counter productive office politics.
Here are just a few of the features available in the Enterprise Edition
Generate professionally formated or fully customized reports instantly in a variety of formats including MS Word, Excel, etc. To protect your Intellectual Property, generated reports are always stored encrypted.
Share your data with others, collaborate with a team on assessments and incidents and have a centralized artifact and vulnerability status repository, and tap into group and community knowledge. Managers can keep track of a team's progress remotely.
If your organization is complex and has multiple groups who have different areas of responsibility. You can easily create reports tailored to each individual group, so that one group can't see another group's issues to avoid any counter productive office politics.
If you have a file too big to send as an email attachment, or if the file contains sensitive informaition that you do not want to send via email, feel free to use the External File Transfer service. This service enables the secure transfer of files over SSL. Once the file is downloaded, it is deleted.
You can create a fully customizable organizational structure that makes sense for your organization. Instantly see which groups are not secure. Handle mergers and aquisitions easily by simply adding new branches and target groups.
The Enterprise Edition of the ThreatConsole can import data from a wide variety of security tools. The vulnerability data can be edited and customized finding descriptions and solutions can automatically be applied to generated reports.
If you need expert assistance on an engagement, consider utilizing ThreatPerspective's Professional Services by contracting our consultants to collaborate on your vulnerability assessment or penetration test. If you are an Enterprise Edition subscriber, you will get a discounted rate.